Ho-Ho-Holiday Hackers: Securing Your Organization’s Information During the Holidays
The tree is up, stockings hung, and lights have begun twinkling in anticipation of another holiday season. What’s that feverish tapping you hear?...
Ransomware and other forms of cybercrime are not going away anytime soon, so it’s crucial to recognize the hacker timeline and prepare for cyber attacks before they occur. The key is to have the ability to respond to threats in real time. For many organizations, their cybersecurity is lacking this crucial aspect. It’s no longer enough to have initial defense systems such as firewalls and antivirus software. Now, businesses need to have a coordinated and efficient incident response plan should a hacker succeed in getting through your network. But curating this plan can be difficult without insight as to how exactly cybercriminals work. Understanding the 5 stages of a hacker’s timeline can help you put effective cybersecurity measures in place to prevent and mitigate network breaches when they do occur.
Cybercriminals use a variety of techniques and tradecraft to infiltrate and exploit a network. Becoming familiar with these methods allows you to recognize the process and put mechanisms in place to stop an intrusion. Below are just a few of the common tactics that hackers use:

To understand how hackers work and move through a network, it is important to know their timeline. This process involves the steps and human behaviors that a person needs to go through in order to attack an organization’s IT environment.
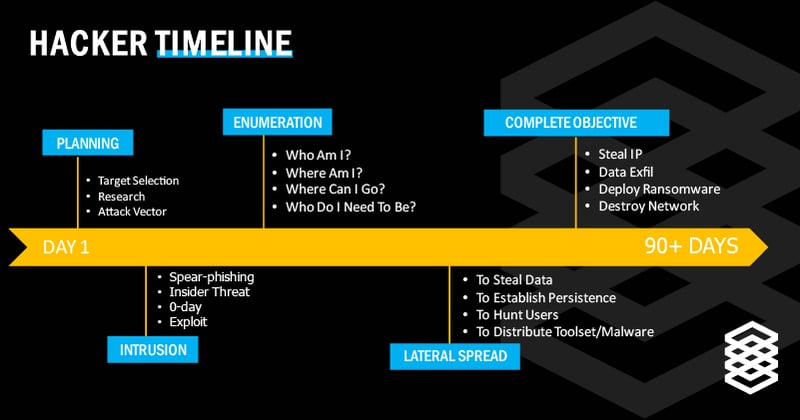
In the early stages of a breach, cybercriminals are usually using techniques to avoid triggering toolsets like endpoint detection and response (EDR), antivirus products, and perimeter defenses or firewalls. Because of this, it can be very difficult to detect when hacker activities are occurring because they are using basic processes that the company and employees use every day to do their jobs. A successful breach could take weeks or months to discover, and even longer to fix the damage done.
So, what can your company do in order to prevent and stop a breach? Cybersecurity best practices including multi-factor authentication (MFA), regular software patching, and employee training are all a good start. However (now that you’re familiar with the hacker timeline), when a breach does occur, the primary goal is to be able to spot the intrusion, enumeration, and lateral spread stages as soon as possible to prevent a hacker from completing their final objective.
To do this, many organizations are adding next-gen technology such as a Security Operations Center (SOC) and Managed Detection and Response (MDR) to stop cyber threats before they can do any harm to the network. SOC and MDR solutions decrease response times to network threats, stopping cybercriminals in the early stages of a hack. By investigating even the smallest inconsistencies and abnormalities, these tools provide the ability to catch problems when they happen and respond in real-time before they cause serious damage.
>With cybercrime on the rise and becoming more sophisticated, it is more important than ever to have layered cybersecurity protocols in place. There is no single solution that will prevent a hacker from exploiting your network – but having multiple preventative measures and “trip wires” in place will decrease your chances of becoming the next victim of a cyber attack.
As a full-service managed security services provider (MSSP), Valeo Networks understands what it takes to restrict unauthorized access, protect your sensitive data, and mitigate breaches before they ever have a chance to derail you. Reach out to us today to schedule a free consultation and learn more about our cybersecurity solutions.



The tree is up, stockings hung, and lights have begun twinkling in anticipation of another holiday season. What’s that feverish tapping you hear?...

Late last week we learned about a massive ransomware attack being referred to as ‘WannaCry.’ This attack is affecting more than 200,000 victims in...

Companies large and small increasingly turn to cloud platforms to run their business and store important information. Keeping this information safe...

With cutting-edge technology and quality customer service,
you’ll find everything you need to help your company soar
with Valeo Networks.
1006 Pathfinder Way
Rockledge, FL 32955
Business Hours:
M-F: 8AM-9PM
© 2026 Copyright Valeo Networks. All Rights Reserved.