How to Choose a Fully Managed IT Services Provider
Every business owner struggles with securing and maintaining all of their business technology. Wouldn’t it be much easier to have a team dedicated to...
1 min read
Valeo Networks : May 5, 2017 12:00:00 AM
This Wednesday, an advanced and convincing computer attack disguised itself as a shared Google Docs message, infiltrating and infecting many news agencies and other institutions systems across the U.S.
Mimicking a Google Docs message, it was sent from a source that looks familiar to most users, such as a friend or colleague. After clicking on the link provided, and then clicking “yes” on a following link, hackers were then granted access to all emails and contact lists available in the victim’s Gmail account.
The attack included many journalists at large organizations such as CNN, The Washington Post, BuzzFeed, Vice Media, and The Wall Street Journal.
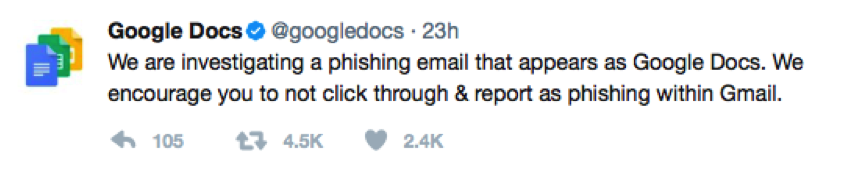
This type of attack is referred to as “phishing,” where hackers disguise themselves online appearing as a valid and credible source.
Once a victim has clicked on the link allowing hackers to access their contact list, the same link is then sent to all people on that contact list, rapidly spreading the attacks.
Google stated that it has “disabled” malicious accounts and has urged updates on current users by pushing them to perform security check ups. “While contact information was accessed and used by the campaign, our investigations show that no other data was exposed,” the spokesperson said.
How can you avoid this attack? While the email itself looks credible and mimics the structure and design of a real Google Docs message, one key giveaway was found. When victims received the email, the email was sent to a fake email (ending in “mailinator.com”) address in the main recipient field, while other users’ addresses were included in the BCC field.
If you have already clicked on the link and granted access to the hackers, Google advises you to visit a security checkup. You can find that information, here.
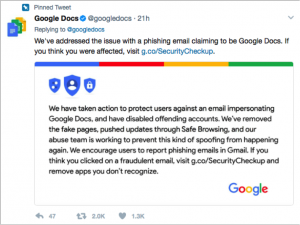 You can also go to your Google connected sites console and revoke access to “Google Docs.” (And don’t forget to change your password!)
You can also go to your Google connected sites console and revoke access to “Google Docs.” (And don’t forget to change your password!)
Need help preventing attacks like these? Valeo Networks would be happy to assist your business’ files and data stay secure. Learn more about Valeo Networks and the services we offer by giving us a call 888-290- 0588 or via info@valeonetworks.com.

.webp)
Every business owner struggles with securing and maintaining all of their business technology. Wouldn’t it be much easier to have a team dedicated to...

Late last week we learned about a massive ransomware attack being referred to as ‘WannaCry.’ This attack is affecting more than 200,000 victims in...

1 min read
The California Consumer Privacy Act and the European Union’s General Data Protection Regulation Affect the Data Protection Policies and Procedures of...

With cutting-edge technology and quality customer service,
you’ll find everything you need to help your company soar
with Valeo Networks.
1006 Pathfinder Way
Rockledge, FL 32955
Business Hours:
M-F: 8AM-9PM
© 2026 Copyright Valeo Networks. All Rights Reserved.