Day 42: Why Your System Security Plan (SSP) Is More Than a Document
With 42 days left, your System Security Plan (SSP) should be more than a formality, it should be a living document that reflects your cybersecurity...
2 min read
Valeo Networks : Oct 17, 2019 12:00:00 AM
Everyone loves a list. This time of the year is full of them: the year’s 10 best movies, 20 best songs, 100 best athletes…you get the idea.
Anyone with a passing interest in cybersecurity over the last five years may have heard of another such list — the CIS Top 20. Unlike the Billboard Top 20, this is not a list of popular tunes. Formally the “The CIS Critical Security Controls for Effective Cyber Defense,” it presents a hit parade of best practices designed to protect a network from hackers and cybercriminals. Think of it as the 20 commandments of cybersecurity.
The Center of Internet Security (CIS) is a volunteer organization comprising hundreds of IT security professionals representing government agencies, military, academia and corporations. According to CIS, its mission is to “identify, develop, validate, promote, and sustain best practice solutions” for effective cyber defense. CIS reviews, refines and verifies the Top 20 Critical Security Controls against today’s most common cyberattack patterns to determine any necessary changes or reordering to the controls list.
These controls are a set of prioritized specific security controls recommended to organizations in order to assess and improve their cybersecurity posture. They cover three separate categories:
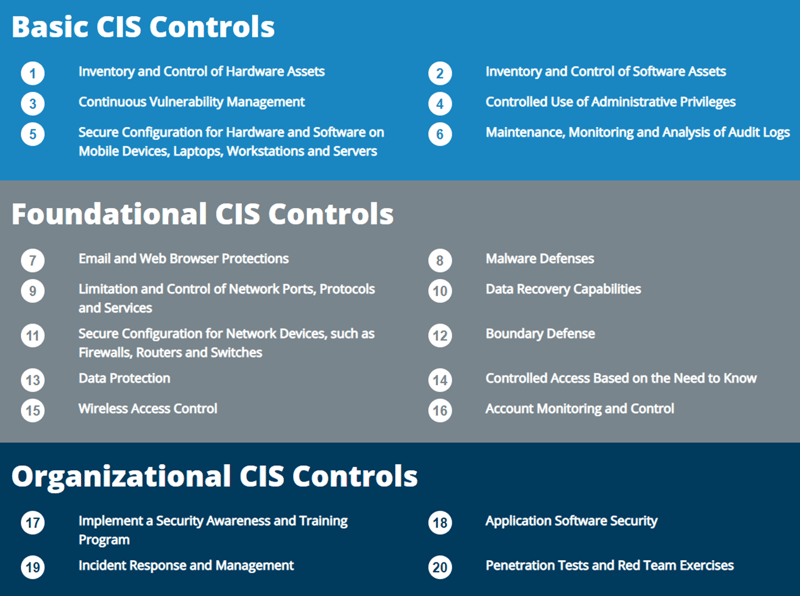
A principle benefit of implementing these 20 Controls is that they prioritize and focus a smaller number of actions with high pay-off results.
While all 20 controls are deemed important, the first six “basic” controls are the most critical in terms of having an immediate, positive impact on an effective cyber-defense.
Organizations that apply just the first 5 CIS Controls can reduce their risk of cyberattack by around 85 percent. Implementing all 20 CIS Controls increases the risk reduction to around 94 percent. (CISecurity.org)
The number one and two critical security controls involve inventorying and controlling hardware assets along with completing an inventory of software. These two security control areas represent the greatest pervasive threat landscape, thus compiling an accurate hardware and software inventory is a vital first step to network security. You can’t implement any controls meant to protect devices and users if you don’t know what you’re protecting.
Control three calls for continuous vulnerability management, because attackers exploit systems when there are gaps in software updates and patches. Organizations must constantly scan for vulnerabilities and address any gaps of which attackers could take advantage.
Control four calls for controlling use of administrative privileges by ensuring those operators have a dedicated account for elevated activities that might otherwise open the door to spread malicious code internally. Additionally, systems should be configured to provide an alert for any changes to administrative privileges.
Control five is secure configuration and control for hardware and software on mobile devices, laptops, and workstations that uses baselines from the CIS benchmarks.
Security control number six includes maintenance, monitoring, and analysis of audit logs. This security control has to do with collecting, managing, and analyzing the details of a security event or anomaly that occurred on a network and captured in an audit log. This will help your team detect future attacks, understand how they happened, and recover from a breach. The use of Security Information and Event Management (SIEM) technology combined with a Security Operations Center (SOC) can provide an invaluable a window to what is happening on your network.
CIS Benchmarks are a set of technical guidelines for hardening operating systems, software applications, and network devices that are most vulnerable to cyber-attacks. The IT community continuously reviews and verifies these guidelines to combat evolving cybersecurity challenges.
Your business can greatly reduce risk and exposure to cyber hacking by implementing these best practices from the CIS Top 20. The combination of CIS Controls and the Benchmarks are the global standard for securing IT systems and data.
Valeo Networks can help your company reduce risk and exposure with a turnkey cybersecurity solution that will align your risk profile with your budgetary and business needs. Contact Valeo Networks for your Cybersecurity Risk Readiness Evaluation.
As presented by Sandy Webster, Cybersecurity Manager, Saalex Corp., “Your Business is Not Prepared for Cyber Threats (and What do Do About it) Webinar.


With 42 days left, your System Security Plan (SSP) should be more than a formality, it should be a living document that reflects your cybersecurity...

The advantages that notebook computers, smartphones and other wireless devices bring work and business are beyond dispute. The benefits of these...

ROCKLEDGE, FL. (June 8, 2017) – Saalex Solutions, Inc., an Engineering and Information Technology Services company, was recently selected as a...

With cutting-edge technology and quality customer service,
you’ll find everything you need to help your company soar
with Valeo Networks.
1006 Pathfinder Way
Rockledge, FL 32955
Business Hours:
M-F: 8AM-9PM
© 2026 Copyright Valeo Networks. All Rights Reserved.